WordPress & SEO Agency
Boost the online marketing performance
of your
MSP Law firm Nonprofit SMB Agency clients
Letting Pronto tackle your WordPress, SEO & PPC projects will save you a small fortune and equip your business with a great website and online presence that works 24/7.







The biggest team of WordPress experts to support your website
CLIENT SHOWCASES
See our work for ambitious businesses
WEBSITE DEVELOPMENT
Your Website Build will start with a unique design that gets people’s attention, provides information, and stands out against the competition. Tell us what makes your company special, and we handle the rest.
STARTING AT $3,500
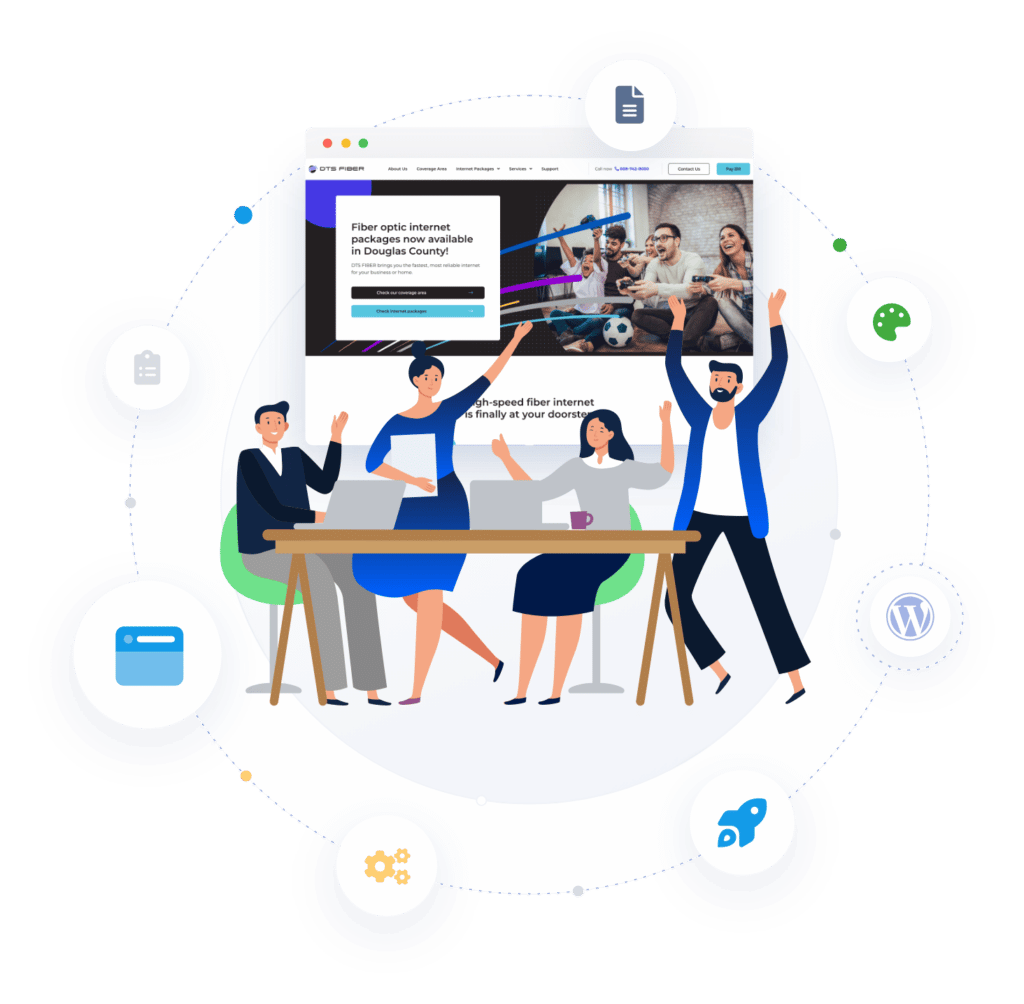

WORDPRESS SUPPORT
We host, maintain, and support your WordPress website
Our website support team is on call 24-hours a day, 7 days a week, covering everything from small edits to large projects to proactive security and platform updates.
STARTING AT $99 PER MONTH
DIGITAL MARKETING
Boost your website with digital marketing add-on services
Grow your online presence with affordable and ready-to-go digital marketing services.
STARTING AT $200
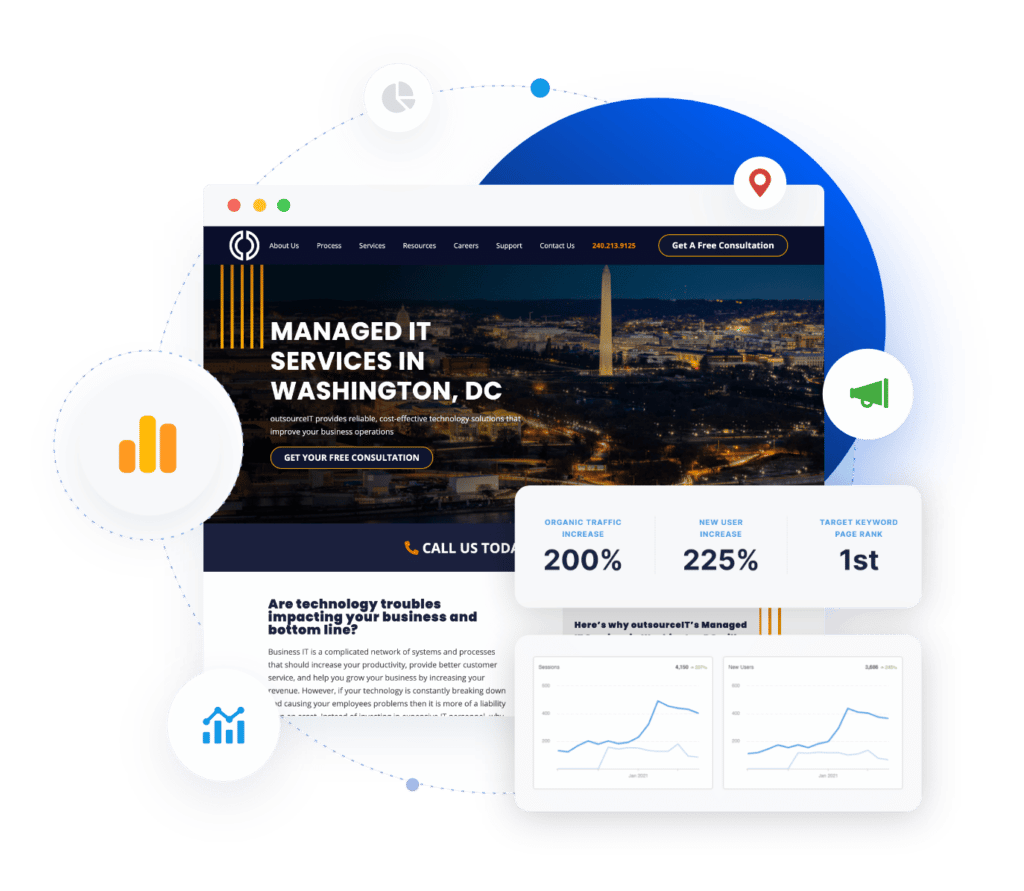
TESTIMONIALS
Trusted by leading professional service firms
What our clients say about how we help them build, support, and promote their websites

Cohen Barnes
Sundog
Pronto gives us a professional website that is regularly updated and search engine optimized.

Kevin LaPorte
LaPorte Law Firm
As an attorney with a heavy caseload, I rely on Pronto to manage the marketing side of my practice. The SEO in my practice areas has improved and so has new clients.

Cynthia Nakid
Operation Noel
Pronto was able to take our site and optimize it perfectly for our holiday campaign. With many orders coming in, we’re thrilled that our site remained stable throughout.



Andreika Meyers
East Coast Repair and Fabrication
Pronto has created and hosted three websites for us, personalized an SEO strategy, provided analytics and reporting, unlimited revisions and copywriting, and 24/7 support. I’ve had a good experience working with them. Their understanding of design is also impressive.

Steven Elkins
CTG Insurance
They were an accommodating and high-caliber team. We liked how Pronto understood our requirements and was familiar with our design inspirations.
Who We Work With

Business Owners
Pronto works closely with small to medium-sized business owners by filtering their industry experience and expertise into impactful online marketing campaigns that boost your presence.

Marketing Staff
Sometimes your marketing staff needs support — that’s where we come in.
Our specialists can expand your in-house team’s capabilities to focus your online marketing efforts in the right direction and drive results.

Agencies & Resellers
Pronto can step in and fill any WordPress design, development or SEO service gap your agency may have.
Through our affiliate program, we offer commissions and annuities for new service sign-ups.
GROWTH CONNECT
Need help with strategy?
Growth Connect is a division of Pronto Group where you can hire a vetted fractional CMO to join your team. Your fCMO will build and lead your marketing team — driving initiatives, coaching team members, and managing the marketing budget — but without requiring the expenditures and obligations of a full-time hire.